Planning Space tenant IdP configuration
PAGE CONTENTS
This topic shows the settings required for the 'Identity Provider' setting for a Planning Space tenant, in the 'Tenants' screen of IPS Manager. Typical settings are shown for different types of IdP.
Each tenant has an independent setting for the Identity Provider (IdP). Click the 'Configure' button to open the dialog named 'Configure SAML2'.
You will need a token (SAML) signing certificate obtained from the IdP server or service.
For version 16.5 Update 7 and later: Some IdP deployments do not require the 'Provider URL' setting. In this case you can insert any text in the input field and it will not be validated, however the field cannot be blank.
(Earlier versions do expect a valid URL to be entered.)
Claim Mapping for auto-provisioning of user accounts (OPTIONAL)
For version 16.5 Update 12 and later: The Configure SAML2 dialog has a second tab for Claim Mapping. This is used in an optional configuration for automatic provisioning of SAML2 tenant user accounts. (This means that a new tenant user account can be created automatically when a user logs in to Planning Space for the first time using an account that is defined, and enabled to access Planning Space, by the Identity Provider's domain authentication services.) For configuration details see Automatic provisioning of tenant user accounts.
Import or Export metadata
These functions can be accessed using the buttons in the tenant configuration dialog (see screenshot below), and simplify the IdP setup process by replacing manual typing. Use 'Export metadata' to get the service provider data (as an XML file) which needs to be loaded into your IdP server or service. Use 'Import metadata' to upload to the IPS Server the IdP settings provided as an XML file or URL by your IdP server or service.
Configuration of Planning Space 'SAML2' user accounts
Every Planning Space user that is based on a SAML account needs to have a tenant user account of type 'SAML2' and the login ID must have a UPN format (in the form 'name@domain.mycompany.com').
It is possible to do bulk import of new Windows user account information into a Planning Space tenant, using the 'Import from CSV' function. For more information see Tenant users and administrators.
Configuration for an ADFS IdP
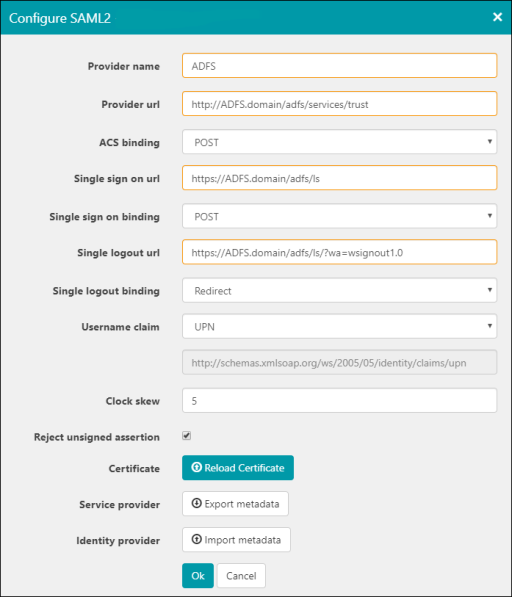
The table shows the standard settings for ADFS.
| Setting | Description |
|---|---|
| Provider name | An arbitrary friendly name for the IdP, e.g. 'ADFS' |
| Provider URL | https://ADFS.domain/adfs/services/trust |
| ACS binding | 'POST' (default setting) |
| Single sign on URL | https://ADFS.domain/adfs/ls/ |
| Single sign on binding | 'Redirect' (default setting) |
| Single logout URL | https://ADFS.domain/adfs/ls/?wa=wsignout1.0 |
| Single logout binding | 'Redirect' (default setting) |
| Username claim | Choose 'UPN' from the dropdown menu |
| Clock skew | Number of minutes time difference allowed between the IdP and IPS machine clocks ( default 3 minutes, range 1 to 60 minutes) |
| Reject unsigned assertion | Enabled (default setting) |
| Certificate | Upload the token signing certificate exported from the ADFS IdP server, in Base 64-Encoded X.509 format |
| Export metadata - Service Provider | Exports an XML file containing the SAML Service Provider metadata which is needed to configure the 'relying party trust' in the IdP server |
| Import metadata - Identity Provider | Imports an XML file that contains the Identity Provider metadata for the SAML configuration |
The following screenshot shows an example of a completed configuration in IPS Manager:
Configuration for an Azure AD IdP
The table shows the standard settings for Azure AD.
| Setting | Description |
|---|---|
| Provider name | An arbitrary friendly name for the IdP, e.g. 'AzureAD' |
| Provider URL | https://sts.windows.net/00.../ [Azure AD Identifier] |
| ACS binding | 'POST' (default setting) |
| Single sign on URL | https://login.microsoft.com/00.../wsfed [Login URL] |
| Single sign on binding | 'Redirect' (default setting) |
| Single logout URL | https://login.microsoftonline.com/common/wsfederation?wa=wsignout1.0 [Logout URL] |
| Single logout binding | 'Redirect' (default setting) |
| Username claim | 'Email address' |
| Clock skew | Number of minutes time difference allowed between the IdP and IPS machine clocks (default 3 minutes, range 1 to 60 minutes) |
| Reject unsigned assertion | Enabled (default setting) |
| Certificate | Upload the SAML signing certificate exported from Azure AD, in Base 64-Encoded X.509 format |
| Export metadata - Service Provider | Exports an XML file containing the SAML Service Provider metadata which is needed to configure the Enterprise Application in Azure AD |
| Import metadata - Identity Provider | Imports an XML file that contains the Azure AD IdP metadata for the SAML configuration |
Configuration for a Citrix NetScaler IdP
The table shows the standard settings for Citrix NetScaler, assuming that there is a NetScaler server at the DNS address 'netscaler.domain.mycompany.com'.
| Setting | Description |
|---|---|
| Provider name | An arbitrary friendly name for the IdP, e.g. 'NetScaler' |
| Provider URL | https://netscaler.domain.mycompany.com |
| ACS binding | 'POST' (default setting) |
| Single sign on URL | https://netscaler.domain.mycompany.com/saml/login |
| Single sign on binding | 'Redirect' (default setting) |
| Single logout URL | https://netscaler.domain.mycompany.com/cgi/logout |
| Single logout binding | 'Redirect' (default setting) |
| Username claim | 'Name ID' (default setting) |
| Clock skew | Number of minutes time difference allowed between the IdP and IPS machine clocks (default 3 minutes, range 1 to 60 minutes) |
| Reject unsigned assertion | Enabled (default setting) |
| Certificate | Upload the SAML signing certificate exported from NetScaler, in Base 64-encoded X.509 format |
